Urgent Security Alert: Shai-Hulud Worm Compromises 500 npm Packages in Widespread Supply Chain Attack

An urgent security alert has been issued regarding a widespread supply chain attack affecting the npm ecosystem, a key part of the JavaScript community. Known as Shai-Hulud, the attack involves a self-replicating worm that has compromised over 500 npm packages, targeting sensitive credentials from major cloud services. Organizations are urged to review their npm dependencies, rotate developer credentials, and implement multifactor authentication. For more defensive measures and guidance on tackling this evolving threat, authorities recommend comprehensive audits and proactive security protocols within software environments.
AI-Driven Ransomware: How Cybersecurity Must Evolve to Combat the Threat

AI-driven ransomware is redefining the cyberthreat landscape, with 80% of attacks now employing sophisticated AI to generate malware, orchestrate phishing campaigns, and perform technical tasks like password cracking. Combating these threats requires not just AI-driven defenses, but also a strategic approach that blends human oversight and technology. Organizations must focus on automated security hygiene, autonomous defense systems, and enhanced oversight. As generative AI becomes integral to both offensive and defensive strategies, cybersecurity experts are urged to innovate continuously to secure digital environments effectively.
Boosting Cybersecurity: How SBOMs Enhance Software Supply Chain Transparency

In a push to enhance cybersecurity across critical systems, several governments have advocated for the adoption of Software Bills of Materials (SBOMs) to illuminate software supply chains and mitigate risks. As inventories of software components, SBOMs provide transparency crucial for assessing security in infrastructures where public safety is paramount. By making vulnerabilities visible and manageable, SBOMs enable swift responses and support secure-by-design practices. Their integration is poised to streamline vulnerability management, reduce costs, and foster a collaborative defense against evolving cyber threats.
FBI Warns of Persistent Cyber Threat from Russian Group Exploiting Cisco Vulnerabilities

The FBI has issued warnings about a cyber espionage threat linked to Russia’s FSB, specifically targeting vulnerabilities in Cisco equipment. Despite patches for these vulnerabilities, many devices remain exposed. The sophisticated group, known for deploying malware and adapting its strategies, has been active for over a decade, focusing on sectors including telecommunications and manufacturing. Organizations are urged to adopt strict cybersecurity measures to defend against these threats. The persistent risk underscores the need for comprehensive defense strategies and international cooperation.
EU Seeks Public Input on Roadmap for Quantum-Safe Digital Infrastructure

The European Commission is seeking public feedback on a new roadmap for establishing quantum-safe digital infrastructure in Europe. This initiative invites input from infrastructure providers, industry stakeholders, academics, and the public to enhance the strategy for transitioning to quantum-resistant systems. The consultation, open until September 29, aims to address sector-specific challenges and leverage open-source tools for broader community benefits. It is part of a comprehensive strategy to secure digital infrastructures as quantum technologies evolve, including plans for a European Quantum Internet and increased research and innovation.
Securing Operational Technology: Combating AI-Driven Social Engineering Threats

The operational technology (OT) sector faces growing threats from AI-driven social engineering, which can disrupt critical infrastructures like energy and manufacturing. Unlike traditional IT breaches, these attacks can lead to operational and safety incidents. As AI tools lower the barriers for attackers, experts urge a rethink of security strategies, emphasizing insider threat monitoring and tailored identity management. The rise of AI-enhanced phishing and deepfake techniques highlights the need for an integrated IT-OT defense and a renewed focus on training to protect vital systems from evolving threats.
Sophisticated Phishing Attack Exploits Japanese Character to Target Booking.com Users
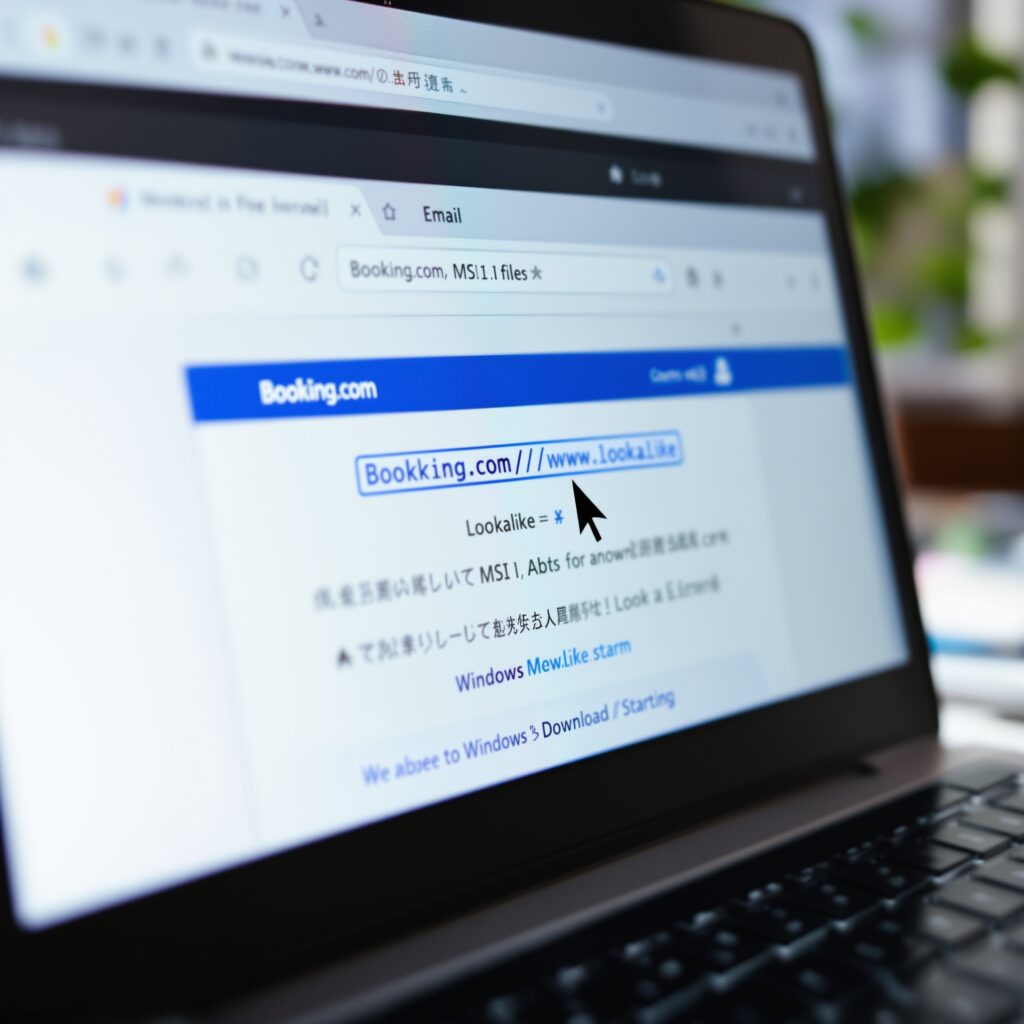
A sophisticated phishing campaign targeting Booking.com users has been uncovered, exploiting the Japanese hiragana character “ん” to mimic legitimate URLs. This clever tactic takes advantage of visual similarities between the character and a forward slash, misleading users into visiting fake websites. These deceptive URLs appear authentic, challenging traditional security measures and emphasizing the need for enhanced awareness and updated cybersecurity strategies.
Security Breach Exposes Backdoor in Docker Images: The XZ Utils Compromise Unveiled

A significant security breach has been uncovered involving a malicious backdoor in Docker images affecting the XZ Utils component. Known as CVE-2024-3094, this breach allows unauthorized remote access through specific vulnerabilities, revealing a possible state-sponsored campaign orchestrated by a trusted developer. With 35 infected images found on Docker Hub, this incident highlights the critical need for robust security frameworks to monitor and prevent supply chain attacks within the software ecosystem.
Estimating the $329 Billion Threat: Securing Operational Technology from Cybersecurity Risks

The cybersecurity risks facing operational technology (OT) systems are escalating, with potential financial exposures reaching $329 billion annually. A recent study outlines various risk scenarios, emphasizing indirect costs from operational disruptions. Manufacturing, chemical, and utility sectors are notably vulnerable. The report advocates for specific OT cybersecurity controls, like incident response plans and network monitoring, to reduce risks significantly. With strong cybersecurity strategies and leadership support, industries can manage these quantifiable risks, safeguarding their operational frameworks.
Navigating Cybersecurity Complexity: Key Strategies for CISOs in the AI Era

In the face of increasing cybersecurity complexity, CISOs are struggling to manage a crowded array of tools and threats, especially as AI technologies become more integrated into corporate strategies. A recent survey highlights the fragmented IT environments that many organizations contend with, impacting security and compliance. The adoption of zero trust models, user-centric security measures, and AI governance are emerging as key strategies, though many companies lag in implementation. With budget constraints as a consideration, there’s a growing emphasis on tool unification, enhanced user experience, and leveraging managed service providers to address these challenges and streamline operations.